[ad_1]
A perfect example of security challenges in remote work occurred when an NTUC employee accidentally downloaded malware to a laptop he used to access corporate files by plugging in a personal USB device. “We received a security alert immediately, but it was difficult to remove,” Lowe recalled. “In fact, we had to send a cybersecurity officer to the employee’s motorcycle home to remove the computer for investigation. In the past, we could protect the network by simply cutting off access to the employee’s laptop. But when an employee works from home, we can’t risk losing any data over the Internet.
Welcome to the new cybersecurity threat landscape, where 61% of organizations are increasing investment in cybersecurity in the era of the home-based pandemic, according to a study by Gartner’s IT program for 2021. Remote workers rely on cloud computing services to do their job, whether they correspond with colleagues, collaborate on projects, or join video conferencing conversations with clients. And when information technology (IT) teams that are already physically removed do not meet their needs, remote workers can easily shop for their own online solutions to problems. But all this bypasses normal cybersecurity practices – and opens up a world of IT worries.
Yet for many regions of the world, remote work is only one of many factors increasing an organization’s exposure to cybersecurity breaches. The Asia-Pacific region is no exception, with 51 percent of MIT Technology Review Insights and Palo Alto Networks surveyed reporting a cybersecurity attack stemming from an unknown, unmanaged, or poorly managed digital asset.
Making a complete inventory of Internet-related assets and restarting cybersecurity policies for today’s modern remote work environment can reduce risks. But organizations also need to understand the trends and challenges in cybersecurity that define their markets, many of which are unique to organizations operating in the Asia-Pacific region.
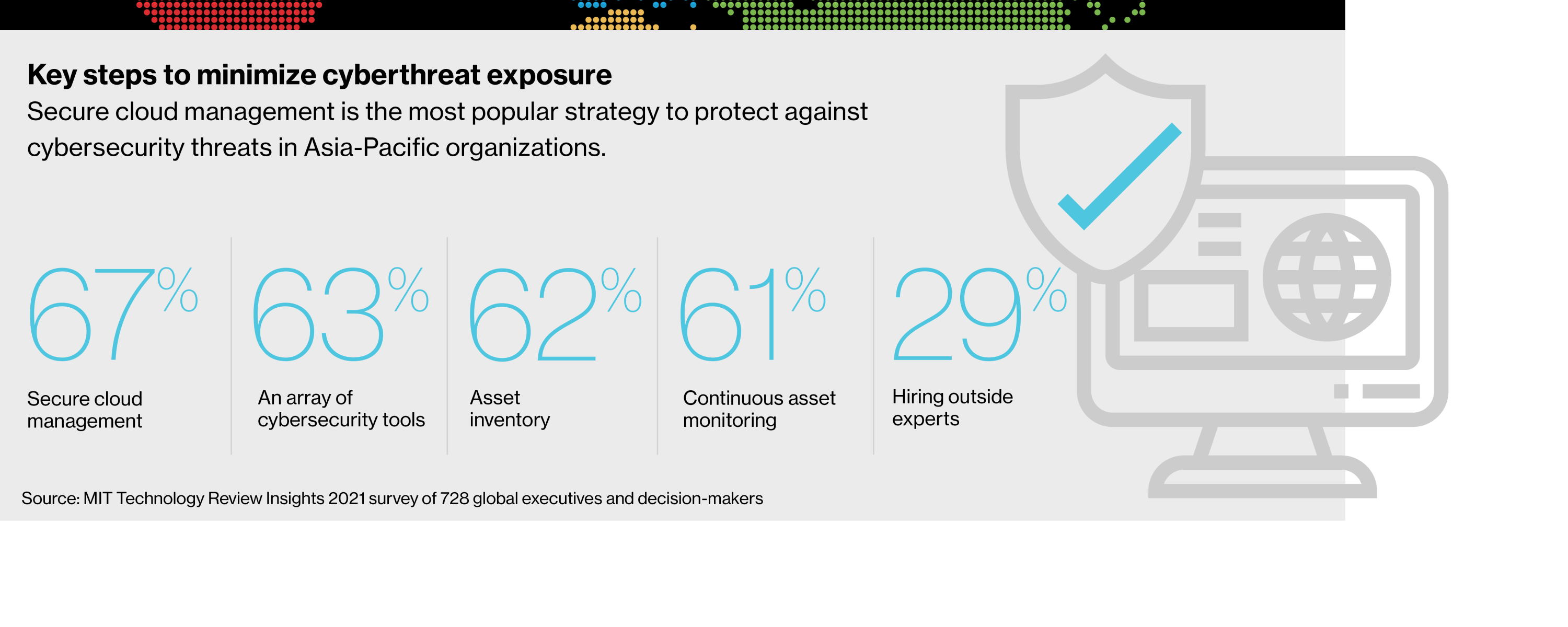
To better understand the challenges facing today’s security teams in the region and the strategies they must adopt, MIT Technology Review Insights and Palo Alto conducted a global survey of 728 respondents, 162 from the Asia-Pacific region. Their responses, together with the input of industry experts, identify specific security challenges in today’s IT landscape and provide a critical framework for protecting systems against a growing battalion of bad participants and fast-moving threats.
Cloud vulnerabilities
The cloud continues to play a crucial role in accelerating digital transformation. And with good reason: cloud technologies offer significant benefits, including increased flexibility, cost savings and greater scalability. Still, clouds are responsible for 79% of the observed exposures, compared to 21% for local assets, according to the Cortex Xpanse Attack Surface Management Threat threat report.
This is a key issue, given that almost half (43%) of Asia-Pacific organizations report that at least 51% of their operations are in the cloud.
One way cloud services can compromise an organization’s security situation is by contributing to shadow IT. Because cloud computing services can be easily purchased and deployed, Loe says, “the purchasing power shifts from the company’s traditional finance office to its engineers. With nothing more than a credit card, these engineers can buy a cloud service without anyone tracking the purchase. “The result, he says, is a ‘blind spot’ that could thwart IT’s efforts to protect the company’s attacking surface – the set of possible entry points. After all, Lo adds,” We can’t defend what we don’t know it exists – it’s an extreme reality today. “
Agnidipta Sarkar of Biocon agrees. “Without the bureaucracy involved in acquiring IT capabilities, shadow IT can grow,” said Sarkar, chief information security officer (CISO) at the Indian pharmaceutical company. “Unless an organization really plans digital sustainability, unplanned and uncontrolled growth in digital assets can escape focused management, which requires information security.”
The exponential growth of interconnected devices is also a challenge for organizations to secure their cloud infrastructure. “Many people are not aware that the Internet devices of things like sensors are actually computers and that they are powerful enough to be used to launch bots and other types of attacks,” warns Lo. He cites the example of smart locks and other mobile applications that allow employees to unlock and open doors – and allow hackers to gain unauthorized access to corporate networks.
While cloud services and interconnected devices raise universal cybersecurity issues, Asia-Pacific organizations face additional challenges. For example, Loe points to the varying degrees of maturity of cybersecurity among countries in the region. “We have countries like Singapore, Japan and Korea that rank high in terms of cyber maturity,” he said. “But we also embody Laos, Cambodia and Myanmar, which are at the lowest end of maturity. In fact, some government officials in these areas still use free Gmail accounts for official communication. “Some vulnerable countries have already been used as launch pads for attacks on neighbors,” Loe said.
Another factor that distinguishes some Asia-Pacific countries from other regions of the world is the unpreparedness to move quickly to remote work in the first months of the pandemic. According to Kane Laitauller, vice president of Cortex, a division of the Palo Alto threat detection platform, organizations lagging behind in their digital transformation efforts “should have prioritized business continuity first,” allowing cybersecurity to take a back seat. . Unfortunately, he adds, “many of these companies have not yet set out to do business in a safe and compliant way. Only now, in 2021, are they starting to prioritize security again. ”
Download the full report.
Find out what organizations in other parts of the world are doing to understand and counter today’s cyber threats.
This content is produced by Insights, the customized content of the MIT Technology Review. Not written by the MIT Technology Review.
[ad_2]
Source link